Command line type hacker. A team of hackers from Russia has developed a method for hacking Skype accounts
Having scored more points at the end of the 33-hour hacker competition than the combined teams in second and third place - PPP from the USA and Dragon Sector from Poland.
Final scoreboard
The 0CTF final was held according to the Attack-Defense rules: teams of security specialists were given the same set of servers with network services specially written for the game, which the participants defend at home and hack at their opponents. Twelve teams from America, Europe and Asia arrived - the best among the nine hundred world teams that participated in the qualifying round.
In the finals, each team managed six services on different platforms: Ubuntu 14.04, Windows 10, CGC (this is an extremely simplified Linux model for the Cyber Grand Challenge - an event where automatic vulnerability detection systems will compete). In each service, the team looks for errors that allow access to information protected by the opponent - the flag. The team urgently closes such bugs at home and begins to exploit them from their opponents. Each successful attack increases the team's rating, and a victim whose service is hacked, on the contrary, loses points. The more vulnerabilities you find and the longer your opponents can’t patch themselves, the more secret flags you’ll have time to steal.
A little about Cyber Grand Challenge
The US Defense Research Agency (DARPA) announced the event in 2013, and over three years, seven systems for automatically searching for vulnerabilities, which analyze compiled programs, generate exploits on the fly, and patch binaries, have reached the final stage. The purpose of the event is to explore the capabilities of algorithms for finding bugs without human intervention, so the environment for running vulnerable programs was simplified as much as possible: everything is in one thread, only data transfer over the network and memory work is available, NX and ASLR protection is disabled.
The CGC finals will take place this summer, and the machine winner will compete alongside human teams at the main competition of the season, DEF CON CTF 2016.
The sixth service, called “polaray,” was different from the others: it was launched not by the participants, but on the organizers’ computer and worked on the principle of the old game Core Wars. Teams upload their pieces of machine code to the jury's server, and it conducts battles between the programs of different teams. The goal of each algorithm is to remain the only program in memory, finding and erasing the code of another program before it has time to do the same in response.
 Day 2 begins: LC↯BC is the first to win Core Wars
Day 2 begins: LC↯BC is the first to win Core Wars The guys from LC↯BC, consisting of six people, were able to hack all the services prepared by the organizers, finding a dozen different bugs in some of them. Thanks to coordinated actions and preparations prepared in advance, the team from Russia took first place in the rating on the first day and gradually increased its advantage until the very end of the competition.
 LC↯BC hold the lead and finish with almost a two-fold lead
LC↯BC hold the lead and finish with almost a two-fold lead 0CTF has a prestigious status this year DEF CON Qualifying Event- victory in the competition, in addition to a cash prize of 40,000 yuan (about 400,000 rubles), brought the Russian team a ticket to the finals of DEF CON CTF 2016, the oldest hacker competition, where, based on the results of the selection, the world's top teams gather to compete in the “season finale” "
The hacker conference DEF CON, like every year, will be held in August at the site in Las Vegas, USA.
Often, inexperienced users perceive the Windows command line as something completely unnecessary and outdated. Thinking like this is a big mistake. The importance of the command line or otherwise the CMD console cannot be overestimated even after it has lost most of its commands available in MSDOS.
The advantage of the command line lies, first of all, in providing direct access to the operating system and its hidden capabilities; in addition, the CMD console has several useful built-in utilities designed for working with software and hardware components of the computer.
Being a command line ace is not at all necessary, however, there are commands that every self-respecting Windows user should know. Here they are.
Assoc
This command is intended to encrypt and decrypt data on drives with the NTFS file system, but it can just as well be used to clear free disk space. It's very easy to use. If you need to be sure to delete the remains of all previously deleted files on drive D, run the command cipher /w:D in the console.
Driverquery
A useful command that allows you to view a list of all drivers installed in the operating system. When a command is executed without parameters, the data is output as a sorted list. The “Module” column contains the names of drivers without extension, the “Name” column includes a brief description of the driver, “Driver Type” - accordingly the type, “Reference Date” indicates the date of installation or last modification of the driver.
FC (File Compare)
The FC command is useful mainly for coders; it can also be used by those users who have to work with text files. This command allows you to compare the contents of two files, looking for inconsistencies between them. Let's say you have two files file1.docx and file2.docx and you want to compare them. Run the following command in the console:
fc /U "D:\file1.docx" "D:\file2.docx"
In this example, we compared two simple text documents. The command line interpreter found a discrepancy in one of the sentences and pointed to the specific location. The FC command also allows you to compare binary files, Unicode files, determine the number of inconsistencies, etc. If the compared files are identical, a corresponding message will be displayed when executing the FC command.
Ipconfig
A useful command that allows you to determine the current TCP/IP protocol settings or simply the IP address. However, it only shows the internal IP address; if you use a router and want to find out the IP with which you access the global Network, it is better to turn to special online services like 2ip.ru.
Netstat
This command lists all current Internet connections. It is mainly used by administrators to display TCP and UDP connections, listening ports, routing tables and statistics for various protocols. It can also be used to search for traces left by viruses and other malicious objects. Running without parameters, the Netstat command displays the connection type, local address, foreign address, and current status.
Ping
Like Netstat, the ping command is used primarily by system administrators. It is used to diagnose computer networks. With its help, you can determine the availability of certain resources. Let's say you need to check the availability of Google. Since Google's DNS server has the address 8.8.8.8, you need to run the ping 8.8.8.8 command in the CMD console.
The digital IP address can also be replaced with a text URL - ping google.com. If the node is unavailable, the message “waiting limit exceeded” will be displayed, and the number of losses will be 100 percent.
Tracert
Another “network” command designed for network diagnostics (tracing). The command allows you to obtain a chain of nodes through which an IP packet addressed to the end node passes. Used by system administrators to identify a problem that is preventing packets from being delivered to an end node. An example of using the command is tracing to a Google node: tracert google.com.
Pathping
This command works in much the same way as tracert, but unlike the latter it is more functional. The command performs a trace plus sending queries to intermediate nodes on the route to collect information about delays and packet losses at each of them.
Powercfg
A powerful command line utility designed to manage Windows power settings. Executed only with parameters. The Powercfg command executed with the /Q switch displays the current configuration of the power supply circuit, with the /a switch it displays a report on the use of electricity in laptops, with the –energy switch it generates a detailed text log about the state of computer components, including batteries. The Powercfg command can also be used to create backup copies of power settings and deploy them to new equipment.
Shutdown
This command is used to log off the user's session, shut down, restart, and hibernate the computer. Supports remote control. Shudown is always performed with parameters. For example, a command like shutdown /s /t 0 will shut down open applications and immediately shut down the computer. You can view the list of available keys by running shutdown /? in the console.
Sfc (System File Checker)
One of the most useful and necessary commands. Designed to detect and restore damaged or modified Windows system files. Restoration is performed from backup copies created by the operating system itself. To run a system scan followed by file recovery, run the sfc command with the /scannow parameter. After the scan is completed, you will need to restart your computer. You need to run this command in a console running as an administrator.
Tasklist
The Tasklist command does the same job as the Task Manager. Executed without parameters, it displays a list of all running processes running on a local or remote computer. At the same time, for each process its name, identifier (PID), session name, session number and allocated amount of RAM are displayed. The Tasklist command supports the use of keys and filters. For example, Tasklist /SVC displays a list of processes along with services for each process individually.
Taskkill
If Tasklist simply displays a list of running processes, then Taskkill terminates them in force mode. True, for this you will need to know the identifier of the process being terminated or the name of the executable file. Let's say you need to force close Notepad. First, run the Tasklist command and look at the PID of the notepad.exe process. In our case, it has a value of 2580. Knowing the PID of the process, you can easily “kill” it. The command itself will look like this: Taskkill /PID 2580. The command Taskkill /IM notepad.exe will work in approximately the same way, only in this example all instances of the notepad.exe process will be terminated.
Bottom line
That's all for now. There are other useful CMD commands that users would like to become familiar with, but we will talk about them next time. These include, in particular, Diskpart - a powerful disk and partition management tool that is not inferior in capabilities to commercial software products such as Acronis Disk Director.
Does it make sense to learn the command line professionally? Unlikely, unless you are planning to become a programmer or system administrator.
However, those wishing to master the CMD console would also do well to pay attention to its advanced analogue - the built-in PowerShell utility.
Good afternoon, readers. Today, once again, I had to go searching for the necessary information. Often you have to help Windows users directly from the user account, and there are no tools at hand other than those built into Windows cmd.exe command line. When working under a restricted account, you often need to perform some task with elevated Administrator rights. cmd for these tasks, the most suitable tool is that you do not have to enter the administrator password many times; you just need to run the command line once as an administrator and perform the necessary actions run the necessary commands which I will describe below:
appwiz.cpl- Installation and removal of programms
certmgr.msc- Certificates
ciadv.msc- Indexing service
cliconfg- SQL Network Client Program
clipbrd- Clipboard
compmgmt.msc- Computer management
dcomcnfg- DCOM component management console
ddeshare- DDE Shares (does not work on Win7)
desk.cpl- Screen properties
devmgmt.msc- Device Manager
dfrg.msc- Disk defragmentation
diskmgmt.msc- Disk management
drwtsn32- Dr.Watson
dxdiag- DirectX Diagnostic Service
eudcedit- Personal symbol editor
eventvwr.msc- Event Viewer
firewall.cpl- Windows firewall settings
gpedit.msc- Group Policy
iexpress- IExpress (I don’t know what it is)
fsmgmt.msc - Shared folders
fsquirt- Bluetooth File Transfer Wizard
chkdsk- Disk check (usually launched with parameters drive_letter: /f /x /r)
control printers- Printers and faxes - does not always start
control admintools- Computer administration - does not always start
control scheduled tasks- Scheduled tasks (scheduler)
control userpasswords2 - Account Management
compmgmt.msc- Computer management ( compmgmt.msc /computer=pc- remote control of PC computer)
lusrmgr.msc- Local users and groups
mmc- creating your own equipment
mrt.exe- Malware removal
msconfig- System setup (autostart, services, etc...)
mstsc- Remote Desktop Connection
ncpa.cpl- Network connections
ntmsmgr.msc- Removable memory
ntmsoprq.msc- Removable RAM operator requests (for XP)
odbccp32.cpl- Data Source Administrator
perfmon.msc- Productivity
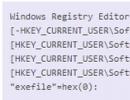
regedit- Registry editor
rsop.msc- Resulting policy
secpol.msc- Local Security Settings (Local Security Policy)
services.msc- Services
sfc /scannow- System file recovery
sigverif- File signature verification
sndvol- volume control
sysdm.cpl- Properties of the system
sysedit - System file editor (don't know what it is)
syskey - Account database protection
taskmgr- Task Manager
utilman Utility Manager
verifier Driver Verification Manager
wmimgmt.msc- WMI management infrastructure
This list is mainly GUI applications. Below I will highlight console commands in a separate list.
You can also run applications in the Control Panel with administrator rights by right-clicking while holding down the Shift key. And select Run as (RunAs...) (relevant for Win XP).
List of console commands:
nbtstat -a pc- username of the user working on the remote PC machine
net localgroup group user /add- Add user to the group group
net localgroupgroup user/delete- Remove user from group
net send pc ""text"" - send a message to a PC user
net sessions- a list of users
net session /delete- closes all network sessions
net use l: \\computer name\folder\- connect network drive l: folder on the remote computer
net user name /active:no- block the user
net user name /active:yes- unblock the user
net user name /domain- information about the domain user
net user Name /add- add user
net user Name /delete- delete user
netstat -a- list of all connections to the computer
reg add- Add a parameter to the registry
reg compare- Compare parts of the registry.
reg copy- Copies from one partition to another
reg delete- Removes the specified parameter or section
reg export- Export part of the registry
reg import- Accordingly, import part of the registry
reg load- Loads the selected part of the registry
reg query- Displays the values of a given registry branch
reg restore- Restores the selected part of the registry from a file
reg save- Saves the selected part of the registry
reg unload- Unloads the selected part of the registry
shutdown- shutting down a computer, you can turn off another one remotely.
SystemInfo /s machine- will show a lot of useful information about the remote machine
The computer world has reached such a scale that today even a schoolchild knows where and how to find something, and some even know how and where they can cause harm. This article will focus specifically on those who are computer security aces. Ace here refers to people who have no limits in the field of computer activities. Many people call these people hackers. Many consider all actions of hackers to be illegal and everything they do is, at a minimum, hooliganism.
Every modern person should be familiar with the word “hacker”. Indeed, lately you can often hear that some Internet resource has been subjected to a massive attack by hackers, as well as how hackers stole confidential information and posted it for public use. Many simply do not know anything about their activities. Now the story will be about the most interesting stories about hackers.
Every hacker is like an artist. His activities require a lot of thought and understanding of the world around him. Often, in order to check which team of hackers is the best, specialized championships are held among hackers. And the pleasant fact is that in 2011, a team of Russian hackers took part in such a competition for the first time, taking place in Las Vegas, and took pride of place.
Wow Holland is one of the most famous people in the computer security industry. And he interprets hackers as people who can think outside the box. It is worth mentioning at least the fact that it was Holland who was one of the ardent sponsors of the notorious WikiLeaks website. He believes that not all hackers are criminals, and many of them only indicate to software manufacturers and heads of large organizations that it is necessary to raise the issue of information security to a higher level than it already is.
One of the most impressive moments in the gaming industry came from Steve Russell, who hacked into a PDP-1 research computer and created a primitive game on it. The size of that computer today shocks people, but at that time it was one of the modern mini-computers. But at that time, Steve Russell was still only a student at MIT (Massachusetts Institute of Technology). Therefore, Russell’s development made a real revolution and gave rise to development in the entertainment industry.

The Massachusetts Institute of Technology owns the brand of one of the best "forges" of hackers. To this day, they teach how to hack computers; in this institution, this subject is perceived as one of the mandatory subjects to study.
Back in 1993, students of this educational institution carried out the largest hack at that time. This hack occurred on the day of a concert dedicated to US Independence Day. Hackers connected to the lighting system of one of the buildings of the Green Boilding educational institution, as a result of which the building became an indicator of the volume of music coming from the speakers at a concert. The lights of this building were turned on at different levels in sync with the volume level. This made a lot of impressions on the part of the city residents.

This joke of Massachusetts hackers was adopted by other craftsmen in the computer industry. In 2001, inventors from the German team Blinckenlights responded to the Boston students. Blinckenlights consists of several members of the Chaos Computer club, which started in the early 1980s. So the members of this team in Berlin used the Teachers' House as a huge display for a simulator of the table tennis game - Pong.
Hackers and politics
Hackers not only create entertainment shows like Blinckenlights and students from the Massachusetts Institute of Technology, but they are also representatives of a political force. For example, US laws do not allow the free distribution of music, films, software, etc. This influenced the development of DVDs encrypted for the redesigned operating system. For example, from DVDs it could only be carried out on a PC with on board or Mac OS. Which in turn deprives users of the freely distributed Linux OS, as well as many other freely distributed operating systems. The year is 1999 and a group of three young enthusiastic hackers led by Jon Johansen began to develop a software product that allows you to view video encrypted in any OS. The program was named DeCSS. It decrypted DVDs and could convert recorded movies into the MP2 open data format. Another distinctive feature of the “good” hackers is that the program written by Johansen was distributed as open source. But already in 2000, a criminal case was opened against Jon Johansen. At the time, Johansen was only 15 years old.
But even in our time, there are hackers who bring great benefits to PC owners. Back in 2010, a group of amateurs hacked the Kinect game controller for the Xbox 360 and announced a competition offering a $2,000 prize to anyone who could write open-source drivers for the controller. Thus, hackers adapted it to work on personal computers. This fact prompted the supergiant Microsoft to release the official version of Kinect for PC.
But there are also negative sides to the development of hacking. According to Symantec, which has become famous as a computer security software company, in the late summer of 2010 alone, a huge number of computer owners (about 100,000) were infected with the Stuxnet virus. The virus spread through and affected computers running the Windows operating system. He gained his fame due to the scandal surrounding Israel, which is suspected of developing this virus with the aim of disrupting the Iranian nuclear program. It was the Israeli roots that were found in the code of this virus. This virus could be used for unauthorized data collection (unauthorized data collection), espionage, as well as sabotage against industrial enterprises, power plants and airports.

Another new trend is the organization of DOS, as well as DDOS attacks on various resources. The most famous hacker group in 2011 was the Anonymous hacker team. These hackers have been attacking such resources for a long time:
- the CIA website (turned out to be unavailable to users for several hours);
- websites of organizations, as well as individuals, that promote laws on copyright, Internet censorship, and oppose “pirated products”
- Various payment systems PayPal, Visa and Mastercard (due to the arrest of the founder of the Wikileaks website);
- Many websites of the Swedish government, as well as the Egyptian government;
- The PlayStation Network website was hacked and completely disabled.
This list can be continued for a very long time. The hackers from the Anonymous team really left a lot behind. Their attacks continue to this day.
Experts from "" estimate the damage from hacking at $100 billion annually. Now we can say for sure that malicious software and hackers have become as much a weapon as soldiers and equipment.
And again about the main thing - let's talk about cmd.exe, which is familiar to you. Even in the newfangled G8, the console has not gone away, and performs all the tasks you are accustomed to and even contains a few surprises.
1. ipconfig command
The most famous and therefore the least interesting in our review. This command is familiar to all “team” administrators and most users: when problems arise with the Internet, technical support staff ask the user to enter it.
The command allows you to view and work with TCP/IP information. You can use it to check a computer's IP address, release or renew the lease on an assigned IP address, and even destroy the local DNS cache.
If you simply enter ipconfig at the command prompt, the command will display information about the IP addresses of all network adapters. For each adapter, a description is displayed, such as “Ethernet Adapter” or “Wireless LAN Adapter,” to make it clear which configuration is shown. A typical set of information contains an IP address, subnet mask, default gateway, and a couple more fields of not very useful information. If you need to get more data, you must use the /all option. In this case, the command will output much more information, and the most useful thing in the expanded output is the “Physical Address” field, that is, the MAC address of the adapter.
In addition to the /all parameter of the ipconfig command, the /release, /renew, and /flushdns parameters deserve close attention. The first allows you to release an IP address assigned via DHCP. True, after this the network will refuse to work, since the network interface will be unconfigured, so the second parameter is useful - /renew, which allows you to update all information assigned via DHCP. This option is very useful because it forces your computer to reconnect to the router or to the provider's servers. It happens that when booting the computer does not see the wireless network (I periodically see this problem on my home computer running Windows 7). Instead of rebooting the computer, it’s easier to enter ipconfig /renew, and the network will appear. The third option allows you to destroy the entire local DNS cache. Sometimes destroying the DNS cache allows you to solve some connection establishment problems, for example, when the DNS information on the server has already been updated, but the old one is still in the local cache.
2. sfc team
The sfc (system file checker) command allows you to check the system file system. This command should not be confused with the chkdsk (check disk) command. Using the latter, you can fix the file system at a lower level and even mark bad sectors. But the sfc command is useful if suddenly some Windows system file is damaged. It can detect this and replace the broken file without any user intervention. Very, very helpful team. It compares thousands of core Windows files to the original versions that came with Windows and, if necessary, replaces damaged or missing files using Windows Update. Depending on how Windows is installed, you may or may not need installation media. Usually it is not needed.
The following useful sfc parameters can be identified:
- /scannow - Performs an immediate system scan and replaces files if necessary. After running sfc, you need to restart Windows if problems are found.
- /scanonce - the scan will be performed the next time the system is restarted.
- /scanboot - the scan will run every time the system is restarted. The Revert parameter allows you to cancel: after experimenting with the /scanboot parameter, you need to run the sfc Revert command, otherwise the scan will be carried out every time you restart.

3. chkdsk command
The chkdsk (Check Disk) command allows you to fix file system errors, detect bad sectors, and restore readable information from bad sectors. Windows checks disks automatically, but you can also run chkdsk manually if you suspect something is wrong with the disk.
As parameters, the command needs to pass the volume name or file name (if you need to check one file or a group of files, in this case you need to pass the file mask). The /F parameter automatically corrects errors, the /R parameter allows you to detect bad sectors and restore information from them. If chkdsk cannot gain exclusive access to the disk, then a disk check will be performed the next time the system boots. This is a common occurrence when trying to check the C: drive. Example: chkdsk D: /R.

4. driverquery command
The command generates a list of all drivers installed on Windows. A good tool that allows you to create reports. The command can be used to examine the version numbers of installed drivers. Based on its results, you can determine whether a particular driver needs to be updated.
The most useful options for this command are /s, /si and /fo. The first parameter allows you to specify the name or IP address of the remote host whose drivers you want to examine. The second parameter shows the digital signature of the drivers. The third allows you to specify the report format: /fo TABLE - table (default), /fo LIST - list, /fo CSV - CSV format, which can be conveniently viewed in Excel or a similar program. Example:
/fo CSV > drivers.csv 
5. Cipher command
This command is used to work with encrypted folders and files on NTFS volumes. Typically, such folders and files are worked through a graphical interface (which is much more convenient), but the cipher command has a very useful /W parameter:
Cipher /W:path
The /W switch (for example, /W:C:) deletes data on unused portions of the volume and effectively erases data on the hard drive after it is deleted. In other words, this command can be used to physically delete data from a disk so that it cannot be recovered by special utilities. It should be noted that this only applies to regular hard drives, not SSD drives. It is believed that files from SSDs are deleted immediately and without the possibility of recovery. Although I would recommend that interested readers read this.

6. powercfg command
The powercfg command controls power settings. It has a lot of parameters, and if you really need to control the power supply from the network, then it is better to use the /? for information about everyone. But most users will be interested in the /a and /batteryreport options. The first command displays a list of drivers that prevent the system from going to sleep, and the second displays a report on battery usage.
7. shutdown command
In UNIX, the shutdown command is used to shut down the system (shutdown, reboot). Few people know, but the command of the same name exists in Windows. Now UNIX fans can shut down the system with shutdown -s and reboot the system with shutdown -r. The -t option is also available to set the shutdown timer (in seconds), for example, the following example will reboot the system after one minute: shutdown -r -t 60. The -f option forces shutdown, closing all running applications.
8. sc command
The sc command interacts with the service controller and installed services. In UNIX/Linux, you can manage services (services, daemons) from the command line (in principle, I don’t know of anything that cannot be done from the command line in UNIX). The sc utility allows you to manage services from the command line in Windows. You can start and stop services, change the startup type of a service, and so on.
So, to start and stop a service, use the start and stop parameters, respectively:
Sc start<имя службы>sc stop<имя службы>
The question arises: how to find out the name of the service? It’s very simple - to do this you need to use the query parameter, as a result a detailed list of all services will be displayed:
Sc query
Since the list is very large, to view it you can redirect the command output either to the more command (for pagination), or to the clipboard (clip command), or to a file:
Sc query | more sc query | clip sc query > services.txt
More information about this command can be found in the sidebar.

9. The recover command
Used to recover information from a damaged or defective disk. Let's imagine that we have a directory d:\reports\2014 and there was a jan.txt file in it, but bad sectors have appeared on the disk, and it is impossible to read the jan.txt file. To restore (partial) information from this file, you can use the command
The recover command reads the file sector by sector and recovers the information that is still readable. It is clear that the program will not be able to take information from damaged sectors, so the recovery of information will be partial. Data from bad sectors will be lost. You also need to remember that using file masks like * and ? is not allowed in this command, you must specify an explicit file name.
10. Tree command
While some may find the tree command useless, it is useful for software developers and technical writers. The tree command displays the directory structure at the specified path. For example, we have a project c:\my_prj\project1. We need to build the subdirectory structure of this directory. To do this, you can use the following commands:
Tree c:\my_prj\project1 | clip tree c:\my_prj\project1 > project1.txt
The first command copies the directory structure to the clipboard, and the second puts it into a file called project1.txt.
PowerShell
In 2012, Hacker published an article called “cmd.exe upgrades and alternatives,” which discussed possible replacements for cmd.exe. Let me remind you that the article discussed console, clink, cygwin, mintty, PowerCmd. All of them make working on the command line more efficient. Microsoft also understood that the standard cmd.exe was already hopelessly outdated, and instead of upgrading it, Microsoft worked on PowerShell. PowerShell is an extensible automation tool from Microsoft that consists of a command-line shell and an accompanying scripting language. The future of the Windows command line is PowerShell, so if you're not familiar with it yet, it's time to get started. We wrote about PowerShell in the February issue.